An error occurred in script '/home/yhr1ef23xez5/public_html/web2/app/model/bannerhit.php' on line 17:
Undefined index: HTTP_REFERER
Array
(
[type] => solution
[name] => bp-Sandbox
)
WinWrap® Basic is an embedded macro language component available for .NET and COM 32/64 bit Windows applications. The WinWrap® Basic Component is an alternative to Visual Basic for Applications (VBA), ActiveX (e.g. VBScript, JScript, PerlScript, Rexx-based WSH engines and others), and VSTA for this purpose. The WinWrap® Basic Component is compatible with VBA, Sax Basic, VB.NET and Visual Basic 6.0 style scripts.
Safe scripting in a .NET application provides powerful .NET script access without compromising functionality. Windows desktop and server applications can be safely scripted by end-users.
Constrain script access to safe .NET functionality when basicNoUIObj.Sandboxed is set to true.
Provide script access to assemblies.
Only members with allowed result and parameter types are allowed (see IsTypeAllowed).
The SandboxRules property and class control script access to the .NET framework.
Block unsafe .NET Framework instructions by setting Sandboxed property. For example, using System.Assembly is blocked at parse-time:
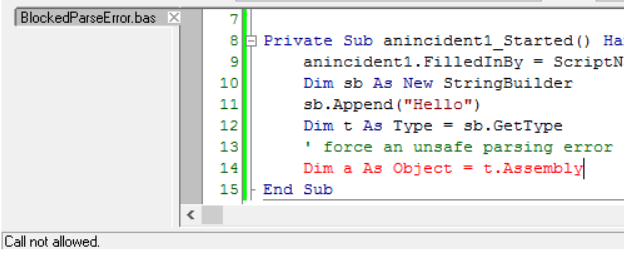
The sandbox rules control exactly what part of the .NET framework is accessible.
Block unsafe run-time instructions by setting Sandboxed property. For example, using late binding to get an instance of System.Assembly is blocked at run-time:
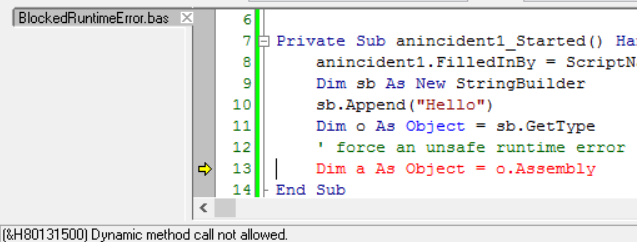
The sandbox rules control exactly what part of the .NET framework is accessible.
Safe .NET Framework functionality, like generic collections, string operations, and Math functions are allowed with Sandboxed = True.
When Sandboxed is True the IDE's autocompletion only shows the types and members allowed.
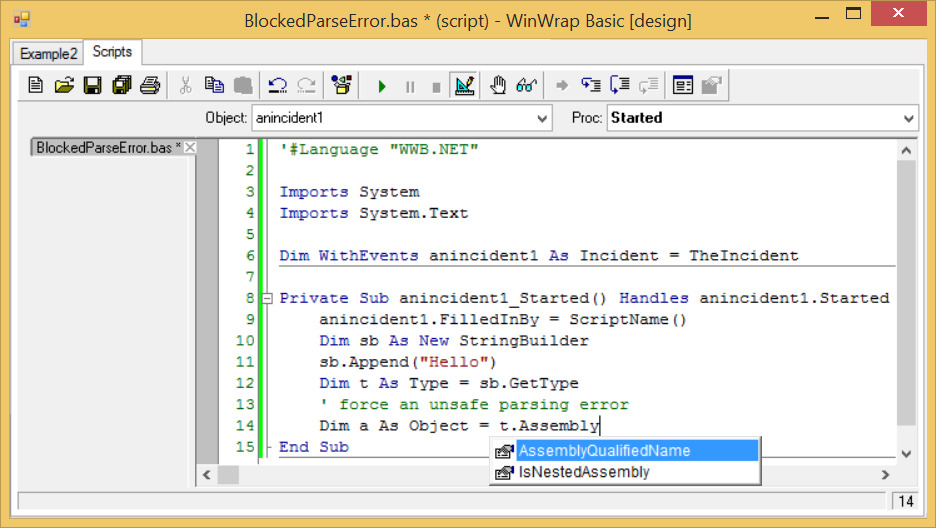
WinWrap® Basic provides a comprehensive solution to adding scripting to your server application.
See WinWrap Examples for instructions on how to download and run "Example 4 - Sandboxing".